Why DDoS Cyber-Attacks aren’t going away

 Denial-of-Service Attacks
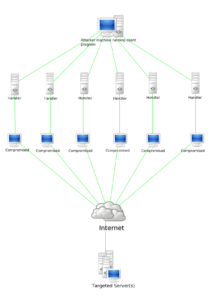
Denial-of-Service Attacks
In computing, a Denial-of-Service (DOS) attack is a cyber-attack where the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.
Why DDoS attacks show no signs of slowing down
Distributed Denial of Service (DDoS) is a type of DOS attack where multiple compromised systems, which are often infected with a Trojan, are used to target a single system causing a Denial-of-Service attack. DDoS attacks have caused substantial damage to organisations across the world.
The code used to cause these large outages was published openly, and soon after all sorts of attacks and variants of the original code were causing havoc around the world.
Detection is too slow
DDoS attacks are not only occurring more frequently but are also becoming even more difficult to detect. Alarmingly, slow detection and response can lead to huge damages financially. Around half of all organisations stand to lose an average of £100,000 per hour of peak downtime during an attack.
Investment is increasing
The increase in DDoS attacks explains why most organisations have now started to increase their investments in DDoS defenses, compared to the previous 12 months.
The threats faced today, and those anticipated in the future, are clearly forcing organisations to completely reconsider the ways they are currently protecting themselves.
Mitigating the Risk of DDoS attacks
Effectively mitigating the risk of a DDoS attack is crucial for organisation that want to avoid financial damage and reputational loss. In order to combat attacks, organisations need to adequately understand the threat, quantify the risk and then create a mitigation plan that corresponds to their needs.
Whether it’s a large or small scale DDoS attack, to keep up with the growing threat, companies will need newer, adaptable, and scalable defenses that include new technology and methodologies.
Developing a mitigation plan
Paying the cost for a DDoS mitigation that exceeds their requirements is like over insuring your car – you are paying a premium for a service that does not match your level of risk/potential loss. Similarly, implementing a DDoS mitigation that does not cover the risk will likely lead to additional costs, resulting from greater organisational impact and additional emergency response activities.
Once the severity of the risk is understood, there are three key critical elements of producing a good mitigation plan that must be enacted: 1) Detection, 2) Response and 3) Rehearsal.
Detecting an attack
There are several technologies out there that can be used to monitor both the physical and cloud-based environment. An example is how organisations can use Netflow monitoring on border routers to detect a volumetric attack, or provide this data to a third-party for analysis and detection.
They can also look at using appliances to conduct automatic detection and response, again managed internally or by a third-party. In a cloud environment, organisations can choose between a vast array of cloud monitoring tools that allow them to identify degradation and performance, CPU utilisation and latency, giving an indication as accurate as possible of when an attack occurs.
Responding to an attack
The response plan to the attack must be scaled to the organisation’s risk exposure and technology infrastructure. For instance, an organisation operating in the cloud with a moderate risk exposure might decide on a cloud based solution, pay-on-occurrence model.
On the other hand, a financial services company that operates its own infrastructure will be exposed to more substantial financial and reputational risk. Such a company would ideally look for a hybrid solution that would provide the best time to mitigate, low latency and near immediate failover to cloud mitigation for large volumetric attacks.
Periodic Testing
Regardless of the protection method being deployed, it’s good practice to rehearse it periodically. Periodic testing can not only eliminate gaps or issues in responding to a DDoS attack, but can also prepare the responsible owners to perform their required actions when an actual event occurs.
DDoS attacks aren’t showing any signs of slowing down anytime soon. The threats associated with DDoS attacks cannot be understated or underestimated. Moreover, by quantifying the risk to the organisation and implementing a right-sized mitigation solution, organisations can effectively and efficiently mitigate the risk of DDoS attacks.



